What Is Cryptocurrency?
Introduction
In short, a cryptocurrency is a form of digital or virtual currency that enables individuals to transmit value in a digital setting. It is a medium of exchange.
The Development of Cryptocurrency
Currency has always been a very essential part of people's lives. In the ancient era, people used the barter system to exchange goods and services with each other. However, due to the obvious shortcomings of the barter system, such as the inconsistency of demand and supply, it was eliminated. For instance, if you have five apples, and your friend has five oranges. You want some oranges, but unless your friend has a demand for the apples you own, you cannot exchange with him. In addition, not all goods can be subdivided or are easy to transport. In essence, the barter exchange system does not have a common value measurement standard that can be used to measure the value of commodities.

After realizing that the barter system could not meet people's requirements, some adjustments were made and the currency was developed to represent the value of commodities. An official currency was minted in 110 BC. From 1600 AD to 1900 AD, paper currency was widely popularized and used all over the world. Modern currencies, including paper currency, coins, credit cards, and digital wallets, are all controlled by banks and governments. In other words, there is a central regulatory authority that regulates how currency and credit cards work. However, centralized authorities or intermediaries may cause certain problems, including their systems being hacked, machines running out of control, or data being controlled and tempered. For instance, if a bank had its database wiped and there were no backups, it would be very difficult to determine users' balances. Therefore, in order to reduce the risk of collapse from the center, blockchain technology, and cryptocurrency were developed.

The function of cryptocurrency is similar to that of real-world currency, except that it has no entity and is a virtual currency. The following are some of the characteristics of cryptocurrencies:
- Decentralized, the issuance, and management of cryptocurrencies are independent of the central authority or intermediary
- The quantity of cryptocurrencies is limited. For instance, the total number of Bitcoins flowing into the market is limited to around 21 million
- Only when certain conditions are met can new cryptocurrencies be generated. For example, in the case of Bitcoin, miners are rewarded with Bitcoin only after a block is added to the blockchain, which is also the only way to generate new Bitcoins

What Makes Cryptocurrency Unique?
- The decentralized nature of cryptocurrency represents that no central authority or subset of users can change the rule without reaching consensus among participants. The network participants are interconnected and share information with each other. Decentralization makes the network highly resistant to shutdown or censorship. Each node on the network keeps a copy of the database.
- Unlike banks that can only operate during business hours, cryptocurrencies can be accessed and traded 24 hours a day, 365 days a year.
- There are no restrictions on the number of purchases and withdrawals.
- Cryptocurrency allows money transfers around the world without intermediary intervention. Therefore, international transactions are faster and have lower transaction costs.
- Cryptocurrencies can be transmitted and traded by anyone with an Internet connection.
Why Is It Called Cryptocurrency?
Crypto refers to cryptography, which is a method of using encryption and decryption to secure information. Cryptocurrency makes extensive use of cryptographic techniques to secure transactions between users.
Public Key Cryptography
Public Key Cryptography (PKC), also known as asymmetric cryptography, is a framework that uses both private and public keys. The use of key pairs provides PKC with a unique set of features and capabilities that have become an important element of modern computer security and an essential component of the growing cryptocurrency ecosystem. This cryptography underpins the cryptocurrency network and provides protection for users to send and receive funds within the cryptocurrency network
A private key is essentially a large, completely random number, which is almost impossible for anyone to guess. Users need to keep their private key secret, and once the private key is lost, they will not be able to access their funds. Eventually, if someone knows your private key, they can easily steal your funds. A private key is similar to a unique signature, proving that you are the owner of that cryptocurrencies. Therefore, the private key is also known as a digital signature. Only when users sign with their private key will their payment information be accepted by others. Therefore, protecting private key information is of vital importance to the user.
In addition, in order to ensure that no one can simply copy one signature to forge another transaction information, generating a digital signature involves functions that rely on the transaction information and a private key. Even minor changes to the transaction information can completely change the signature. Apart from that, in order to verify whether the signature is valid, a public key is required.
Simultaneously, the public key appears to be a string of random numbers. It is generated from a private key by using an Elliptic Curve Signature Algorithm and can be safely displayed to anyone. Then, the address can be obtained by hashing the public key. The public key generated by the Elliptic Curve Signature Algorithm can be paired with the private key for asymmetric encryption. In other words, the keys for encryption and decryption are different from each other. Anyone can use the public key to determine whether the private key is matched and valid, while it is not feasible to calculate the public key in the reverse direction to obtain the private key.
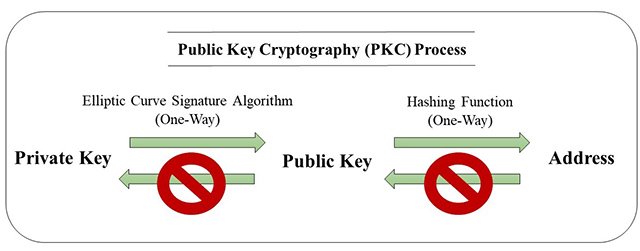
In the case of Bitcoin, the private key is used to encrypt information, while the public key is used to decrypt it. The address obtained by the hash calculation of the public key represents the user's account, and the coins stored on this address are controlled by the private key. For example, if Bob plans to give Jack a bitcoin, Bob's address is A, and Jack's address is B. Bob needs to hash the transaction data, "address A sends a bitcoin to address B", and then encrypt the resulting hash value with the private key. Subsequently, the encrypted information is broadcast on the network together with the public key of address A. In order to verify the validity of the information, Jack can hash the obtained public key and compare whether the result is consistent with address A. In addition, the public key can be used to decrypt the encrypted information into a hash value, while the transaction information can also be hashed to obtain a hash value. Comparing the two resulting hash values and if the hash values are the same, indicates that the information was indeed sent by Bob and has not been tempered.
Find us on:
Telegram: https://t.me/coincarp
Twitter: https://twitter.com/coincarpcom
Facebook: https://www.facebook.com/coincarpcom
Wordpress: https://coincarp.wordpress.com/
Blogger: https://coincarpcom.blogspot.com/
Medium: https://medium.com/@coincarpcom
Reddit: https://www.reddit.com/r/CoinCarp
Comments
Post a Comment